We probably aren’t the first to tell you that SAP Fiori provides many benefits to organizations. You might have even heard other organizations rave about Fiori’s new user-friendly interface or the ability to use SAP from any device and location. We agree that there are many benefits.
But like any data that is exposed to the Internet, security is an important consideration. Don’t let this be a deterrent! With the help of this guide, you will gain important insights into tightening up your own security practices and preparing to bring a better user experience to your users with SAP Fiori.
How is SAP Fiori Deployed?
With SAP Fiori, users are presented with a modern user interface (UI) with access to the data that they need in the backend systems. Here is a diagram of the high-level architecture diagram of a typical Fiori implementation.
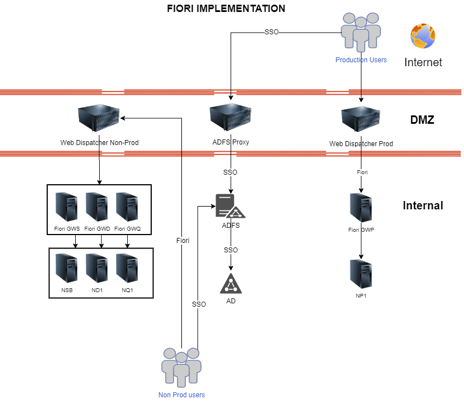
This diagram illustrates the connectivity between devices in a scenario where Fiori users can connect from anywhere (including mobile devices!), the steps below describe how it works.
- The user initiates a request to access the Fiori launchpad. This might be through the SAP Fiori Client on their phone, or by accessing the Fiori URL for their company.
- The request for access comes to the Reverse Proxy (Web Dispatcher) in the DMZ (Demilitarized Zone). It handles requests from the external world and routes them to the appropriate internal servers. In this case the next stop is the SAP Gateway (Fiori GWP in the diagram).
- When the request reaches the Gateway, it can go no further until the authentication requirements are met. We recommend that organizations enable single sign-on (SSO). It provides additional security by validating users through a centrally administered active directory (ADFS Proxy / ADFS in diagram) – and users appreciate it because they are not re-entering credentials!
- When all of the requirements are satisfied, the user is granted access to the Fiori Launchpad. All of the connections are SSL (Secure Socket Layer) enabled, so the traffic is encrypted too.
While your users are busy appreciating the intuitive and straightforward Fiori interface, your organization can rest easy knowing that the system is secure.
Security Best Practices
In order to secure Fiori properly, we must make sure we are considering each layer that is involved. These layers include:
-
SSL communications: All the communications must be configured using SSL with proper certificates. This is a key and mandatory action. Especially since failing to use SSL will expose your confidential data.
-
Proxies / Load Balancers: Reverse proxies/load balancers on the DMZ act as a barrier from the external world to the internal network. These servers forward the Fiori traffic to the appropriate internal servers and provide an extra layer of security.
-
Firewalls: Firewalls need to be used to allow only the traffic that we want and call ports are closed except the ones used by Fiori. This can vary depending on the organization, but at least an external and internal firewall is recommended.
-
Single Sign-On: Make sure all users connect to a central repository database that can be easily monitored and maintained. With the proper configuration, the Fiori environment can be configured to only allow single sign on (SSO) connections (and correspondingly disabling the less secure “basic” login to the Fiori Launchpad).
-
Two-Factor Authentication: When integrating sign on with Azure (for example) two-factor authentications can be enabled to provide another layer of security. This secondary verification of users greatly increases the overall security.
-
SAP Gateway Security: It is also important to properly secure the SAP Gateway. This means understanding and properly configuring the system parameters to disable different threats from the outside. In addition, it means creating proper roles with specific functionality and always following the SAP best practices for user security.
-
SAP Backend Security: In combination with the Gateway, the backend needs to be properly designed for user security. You need to make sure you properly design all of the roles so the different types of users have only the roles necessary to access their data.
-
Monitoring Network: Enabling monitoring tools for network interfaces. It is important to have tools that monitor all the incoming traffic and detect treats and configure them to automatically notify you when threats are detected.
A Final Word
SAP Fiori is an evolution for SAP. Why can we say this? It allows you to access your data in real-time from your mobile devices and with a proper security setup, careful monitoring, and abiding by the best practices that we outlined in this post, you can feel safe knowing that your data is secure.
To learn more about how SAP Fiori can be tailored to your business’ needs, check out how Halton Region used SAP Fiori to transform their purchasing process.

