As companies start to migrate to cloud services like SAP BTP Launchpad Service, there are some security aspects that need to be addressed. In this blog, we are going to talk about the security elements of using a Hybrid scenario between BTP services, such as the Launchpad Service, and on-premises systems with Identity Authentication Service (IAS) / Azure Active Directory (AD) as the Identity provider.
For example, we have company A that has a fully working on-premise Fiori Launchpad with no external access, meaning only users in the internal network can access it. They are looking for solutions to expose certain Fiori applications externally to end users and have it accessible on their mobile devices. The company is concerned about exposing the whole Fiori Launchpad to the internet.
For the solution, we will use the SAP BTP Launchpad Service to enable specific Fiori applications using content federation from our on-premise systems or, in other words, exposing some of the Fiori apps into SAP BTP Launchpad Service so we can access them externally.
Here is a diagram of the solution:
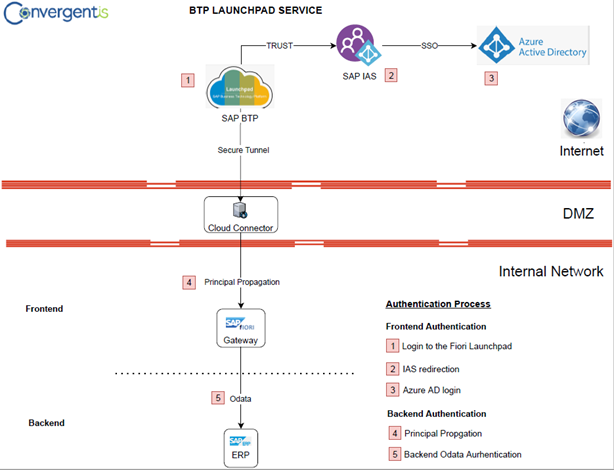
We are going to assume the configuration of the BTP Launchpad Service has been done, check out this blog with more information on how to set it up.
Authentication Process
First, we will explain how the users are authenticated. The user will be given a Fiori Launchpad URL that we can access from any device. We can set some access controls that we will explain later. The authentication happens in two steps. First, it is the Front-end authentication, which is where the user will log in to the Launchpad Service and get access to the Fiori Tiles. Once the user clicks on the URL, they will be redirected to the IAS, and from there use single sign-on (SSO) to the Azure AD. The user will be presented with the following login:

Companies can leverage this in Azure AD to enable all the security controls, such as Two Factor Authentication (2FA) and conditional access (device types, IPs, locations, etc.), to name a few. This is important because the SAP Launchpad will continue to use the existing security controls that the company is using with Azure AD.
Once logged in successfully, we will see the Launchpad with the Tiles.
The second part of the authentication process is the backend authentication. Here we will get access to the data from the backend. This part must be transparent to the end users through the process of principal propagation. To explain this concept, we are going to propagate certain Security Attributes from Azure AD using Security Assertion Markup Language (SAML). For example, if you are already logged in using Azure AD, your security information can be propagated using SSO to the SAP backend via the cloud connector. The security information will be sent to the backend in the form of a certificate. The backend will match these security attributes and identify the user.
Security Controls
Now, lets talk about all the security controls that we can establish at the different layers.
Identity Authentication Service: The IAS can act as a whole identity provider itself. Here we can configure Risk-Based Authentication (RBA), which includes specific controls such as Internet Protocol (IP) address, authentication methods, user type and multifactor authentication.
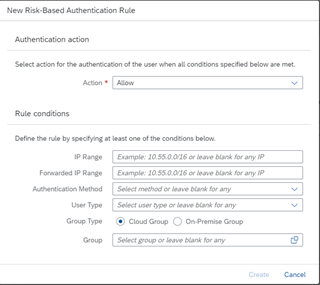
This makes sense when the company is fully in control of the Active Directory as their Corporate Identity Provider. However, if you are using the Cloud-based Azure AD, the only feasible option to leverage these controls is through the Microsoft Platform.
Azure AD: Azure comes with extended sets of controls that can limit access in many ways. For example, for Company A, only mobile devices included in the organization will have access. When a user does not meet these requirements, they will be presented with an error. Network/Security teams will be able to enable these controls as per the requirements. Here we can see a link to different controls in Azure.
SAP Business Technology Platform: On the BTP side we have role collections. Depending on how we have created the content, these role collections will enable different Fiori applications. Users need to be assigned these role collections to see the different tiles. In a test environment, it is fine to do these manual tasks, but in a production environment it is recommended to take advantage of the SAP BTP feature Role Collection Mappings. With this feature, we can automate the user creation and role assignation leveraging the SAML Azure AD attributes. For example, we can create a rule for which all users that belong to an Azure AD Group called “Managers” will be assigned the role collection “BTP_MANAGERS”. This way, all the security is handled on the Azure AD side.
You can find more information on this topic in my blog related to Role collection mappings.
Cloud Connector: The cloud connector acts as the conduit for connections between SAP BTP and backend servers within internal networks. During the initial configuration, the cloud connector establishes a secure encrypted tunnel to the BTP subaccount. This connection can happen directly from BTP to the backend system, or you can establish an indirect connection through an internet proxy as a way of further enhancing security. From the cloud connector to the application servers, we create destinations to our backends, including the possibility to add another reverse proxy between our application servers. To make systems secure we must make sure SSL is always used. Also, the cloud connector is a great place to restrict the types of resources that can be accessed from the BTP services. See the example pictured below.
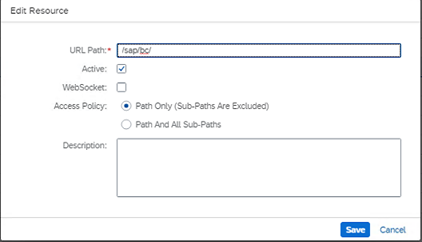
Below is an example of connection monitoring.
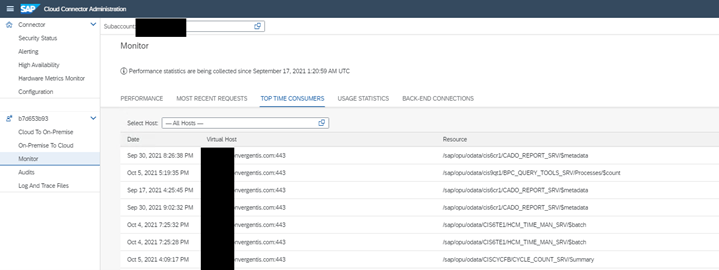
The principal security propagation also occurs here. The cloud connector creates the user certificates that eventually will be used for authentication in the backend.
Gateway and Backend: As the last layer of security, we have the SAP system, with its own security controls as we use currently in our On-premise Fiori Launchpad.
Conclusion
Exposing our systems to the internet can warrants concern. However, using BTP brings many benefits to our organizations. There are many controls that we can utilize to secure and monitor our cloud systems and connections. Also, we can integrate our existing security protocols into the SAP BTP solutions.
For more information, we encourage you to contact us for more information.

